Connecting with Excellence: Regional Managed Service Providers Near Me
Connecting with Excellence: Regional Managed Service Providers Near Me
Blog Article
Strategize and Scale WITh Proven IT Managed Providers Techniques
In the hectic landscape of modern organization, the calculated usage of IT handled solutions has actually come to be a keystone for companies aiming to improve operational effectiveness and drive lasting growth. By executing tried and tested strategies tailored to satisfy certain business needs, companies can navigate the complexities of innovation while continuing to be dexterous and affordable in their respective industries. As the demand for scalable IT remedies remains to rise, understanding how to effectively plan and utilize took care of services has never been a lot more essential. It is within this world of development and optimization that organizations can really open their potential and pave the way for future success.
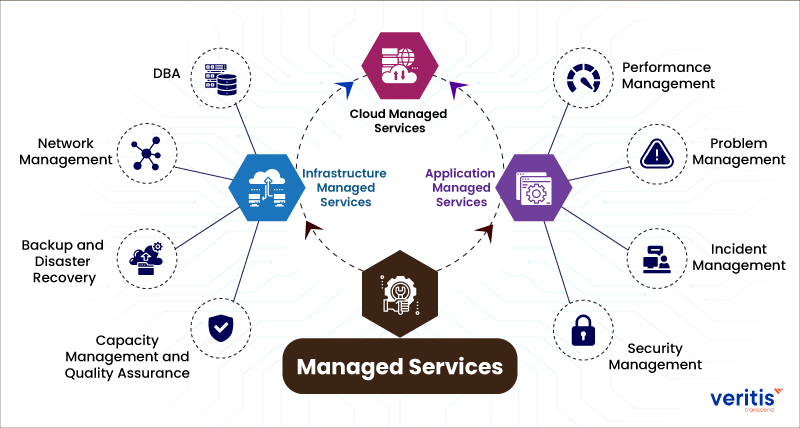
Benefits of IT Managed Solutions
Undoubtedly, the benefits of IT Managed Solutions are vital in enhancing organizational effectiveness and decreasing downtime. By outsourcing IT management to a specialized supplier, companies can touch into a wide range of know-how and sources that would or else be expensive to maintain internal. One of the vital advantages of IT Handled Services is aggressive surveillance and maintenance of systems, which aids avoid possible issues prior to they escalate right into significant problems. This proactive strategy converts right into improved system uptime, reduced downtime, and enhanced overall productivity for the organization.
This makes certain that organizations continue to be competitive in a quickly advancing technological landscape. In final thought, the advantages of IT Managed Services are crucial in enhancing operations, enhancing effectiveness, and inevitably, driving company success.
Trick Methods for Implementation
With an understanding of the significant advantages that IT Took care of Solutions deal, organizations can now concentrate on implementing crucial techniques to successfully integrate these solutions right into their operations. One crucial technique is to clearly specify the extent of solutions needed. This includes carrying out a thorough evaluation of existing IT framework, determining pain factors, and setting particular objectives for enhancement. Additionally, organizations have to develop clear communication networks with their handled provider to ensure seamless collaboration and prompt concern resolution.
An additional vital strategy is to focus on cybersecurity steps. Information breaches and cyber risks posture significant risks to organizations, making safety a leading priority. Implementing durable safety procedures, normal surveillance, and timely updates are important steps in protecting sensitive info and keeping company continuity.
In addition, companies need to develop service degree arrangements (SLAs) with their handled service provider to specify expectations, duties, and performance metrics. SLAs aid in setting clear standards, ensuring accountability, and preserving solution high quality standards. By including these essential techniques, organizations can utilize IT Handled Services to simplify operations, improve performance, and drive sustainable growth.
Maximizing Effectiveness Via Automation

Additionally, automation her latest blog enables real-time monitoring and data evaluation, offering useful insights for notified decision-making. By automating routine surveillance jobs, organizations can proactively attend to issues before they intensify, reducing downtime and enhancing efficiency (managed service providers). Additionally, automation can assist in the smooth assimilation of different systems and applications, boosting partnership and information flow across the organization
Ensuring Information Safety and Conformity
Data safety and security and conformity are paramount worries for services operating in the digital landscape of today. With the boosting volume of sensitive information being saved and processed, guaranteeing durable safety and security steps is important to guard against cyber threats and abide by regulatory needs. Carrying out thorough information safety methods includes securing information, establishing accessibility controls, routinely upgrading software, and performing safety audits. Conforming with laws such as GDPR, HIPAA, or PCI DSS is necessary to keep and prevent pricey charges depend on with customers. Handled IT providers play an important duty in aiding organizations navigate the complicated landscape of data security and conformity. They use expertise in carrying out protection protocols, checking systems for potential breaches, and guaranteeing adherence to market regulations. By partnering with a respectable took care of providers, businesses can boost their data safety and security posture, mitigate dangers, and show a commitment to securing the confidentiality and integrity of their data assets.
Scaling IT Infrastructure for Development
Including scalable IT facilities options is crucial for promoting company growth and operational effectiveness. As business expand, their IT needs advance, requiring facilities that can adjust to enhanced demands flawlessly. By scaling IT facilities efficiently, companies can ensure that their systems stay dependable, secure, and performant even as work expand.
One key aspect of scaling IT infrastructure for growth is the capability to flexibly assign sources based on present needs. Cloud computer solutions, for instance, deal scalability by allowing services to adjust storage, refining power, and other sources as needed. This elasticity makes it possible for firms to effectively manage spikes in need without over-provisioning sources throughout durations of reduced task.
Additionally, implementing virtualization technologies can boost scalability by making it possible for the development of online instances that can be easily copied or customized to fit transforming work - managed service provider. By virtualizing servers, storage space, and networks, organizations can maximize resource utilization and improve IT management procedures, inevitably supporting organization development efforts effectively
Conclusion
In verdict, executing IT took care of services can bring countless benefits Visit Website to a company, such as raised performance, enhanced information protection, and scalability for development. By following crucial approaches for implementation, utilizing automation to maximize efficiency, and guaranteeing information protection and compliance, companies can much better strategize and scale their IT framework. It is important for companies to advance and adjust with technical developments to stay competitive in today's ever-changing landscape.
Report this page